LAST UPDATED: 06/05/2020
“We’ve been breached and millions of records are in the hands of attackers. But don’t worry; we promise to do better.”
This is a headline that has been published on a seemingly weekly basis over the last few years. Multi-million and multi-billion dollar companies publish vague press releases notifying the public of a data security breach with guarantees that they will learn from this experience so that it can’t happen again.
Uber, Capital One, Marriott, and British Airways are a few companies whose well-publicized data breaches compromised the sensitive information of millions of their customers due to poor security practices. If you believed their press releases, however, you would think that these were abnormal events. That these companies have rigorous data protection policies in place and that bad actors managed to find a backdoor entrance.
Surely in an industry like credit card payment processing, which has had rigorous data security standards for nearly two decades, the vast majority of companies that handle sensitive information would be compliant? Unfortunately, this graph (Figure 1) tells a very different story.
Every year, a division of Verizon publishes a “Payment Security Report.” In the 2019 report, their team analyzed data from over 300 representative organizations in the Americas, Asia Pacific, Europe, the Middle East, and Africa. They worked with organizations that spanned several industries: finance, hospitality, retail, IT services, and more.
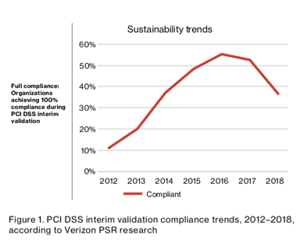
They found that only about 36% of companies are in full compliance with the Payment Card Industry Data Security Standards (PCI DSS). And what’s most worrisome, is that the percentage of companies in full compliance has been trending downward since 2016.
This means that despite the weekly breaches dominating the headlines, organizations that accept payment card data are actually decreasing their efforts around data security.
What Is PCI Compliance?
In 2006, several major credit card companies (Visa, MasterCard, AmEx, and Discover, among others) decided to merge their proprietary data protection standards into what came to be known as PCI DSS. The goal was to provide a single set of comprehensive guidelines that organizations using payment card data would have to follow, rather than have different card types requiring different protections.
PCI DSS has six groups of “control objectives”:
- Build and Maintain a Secure Network and Systems
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
Organizations that handle credit card data can fall under one of four levels of PCI compliance. These levels are based on the number of transactions processed per year. Level 4 is the lowest, for organizations processing less than 20,000 transactions annually, while Level 1 is for those that process more than 6 million transactions annually.
What Makes PCI Compliance So Challenging?
In testimony before the House of Representatives Subcommittee on Cybersecurity in 2009, the CIO of Michael’s stores made the following statement:
“The PCI Data Security Standards are an extraordinarily complex set of requirements. They are very expensive to implement, confusing to comply with, and ultimately subjective, both in their interpretation and in their enforcement. It is often stated that there are only twelve ‘requirements’ for PCI compliance. In fact, there are over 220 sub-requirements; some of which can place an incredible burden on a retailer and many of which are subject to interpretation.”
It doesn’t take much analysis to see the validity to this CIO’s point — the regulations are:
- Complex: In one of the more detailed sections of the PCI standards, under Control Objective 3 for Protecting Stored Cardholder Data, you run into terms like cryptographic key management, one-way hashes, and PAN truncation. Not only would these be completely new to most companies that have to comply with PCI DSS, but they wouldn’t even be able to find any helpful definitions within the regulation. These are things that, prior to PCI DSS, only central banks and the military had to worry about; all of a sudden, it became a problem for a much larger group of companies.
- Expensive: Many of the compliance solutions available right now charge companies on a per-transaction basis: the more credit card transactions your organization handles the more their data protection solutions cost you. Many of these solutions have appealing deals with low up-front costs, rapid deployment in the cloud — everything to make it quick and easy to sign on with them. Very soon, however, the problem shifts from complying with PCI DSS to paying for compliance.
- Subjective: Even if your company has all the proper policies and procedures in place for compliance and is spending the money it takes to sustain them, there is still a chance that they might not be considered compliant. This is because the compliance decision rests fully with Qualified Security Assessors who conduct the audit. Different QSAs have varying levels of experience and may have different levels of familiarity with certain technologies. The breaches mentioned above at Capital One and Uber were not the result of hackers breaking down defenses, but rather, bad actors taking advantage of simple misconfigurations in their environments. These are things that should have been spotted by QSAs, but clearly were not.
The Verizon report suggests that as a response to these vague and subjective guidelines, companies have embraced the “checklist” attitude towards data protection — that if they follow a certain number of steps, then they are sufficiently covered. Unfortunately, this only provides a false sense of security, and is the primary reason why the vast majority of companies would not be considered PCI compliant.
Strategies for Improving PCI Compliance
Although these downward trends and frequent headlines seem disheartening, there are a handful of very clear and immediate steps your organization can take to move towards sustainable PCI Compliance.
- Isolate Sensitive Data: Once you have a clear picture of how sensitive data is flowing around your different applications, limiting the places in which it is used would be the best first step you can take. This can be accomplished by tokenizing the sensitive data and using it as a pointer, rather than duplicating the actual piece of data in various applications. If you can cut down on applications that rely on sensitive data and make use of tokenization instead, the points of entry for any attacker are sharply reduced.
- Ask the Experts: There are a number of companies who have been helping companies achieve PCI Compliance for over a decade. They have learned along the way which strategies work and which don’t. Experts will be able to suggest industry best practices that go above and beyond the PCI regulations to ensure the strongest data protection strategies are being used.
- Make Use of Cryptographic Hardware: Although this is not specifically mandated by the PCI regulations, using cryptographic hardware to store and manage encryption keys is one of those industry best practices mentioned above. There are several reasons why key management in the cloud is never going to be secure, all of which are solved by using cryptographic hardware. Another benefit of this is that you can avoid paying per-transaction fees by relying on this hardware for encryption and tokenization making it an accessible tool to companies of all sizes.
StrongKey has been helping companies pass PCI DSS audits for over a decade. Contact us to get personalized recommendations for your organization.
Continue to Twitter Hack in Bitcoin Scam Reveals Fundamental Security Flaw.


